China-linked hacking group FamousSparrow seems to be back in action after several years of inactivity –- and with a revamped cyber arsenal.
According to an ESET report published on March 26, FamousSparrow recently compromised several organizations in the US, including a trade group in the US financial sector, a research institute in Mexico and a governmental institution in Honduras.
This advanced persistent threat (APT) group, widely believed to be backed by China, was considered dormant since its last activity in 2022.
This new report suggests that this may not have been the case.
Tracking FamousSparrow Cyber Espionage Activity
FamousSparrow is a cyber espionage group that has been active since at least 2019.
ESET Research publicly documented the group for the first time in a 2021 blog post when it was observed exploiting the ProxyLogon vulnerability.
Initially recognized for targeting hotels worldwide, the group has since expanded its operations to include governments, international organizations, engineering firms and law firms. Notably, it is the only known actor to employ the SparrowDoor backdoor.
However, FamousSparrow appears to have connections with several other Chinese-backed APT groups.
In 2023, Trend Micro observed that a cyber espionage campaign against government and tech organizations, conducted by Earth Estries, included many similar techniques to those of FamousSparrow.
In September 2024, in a Wall Street Journal article about the Salt Typhoon cyber espionage campaign which targeted US telecommunications providers, Microsoft claimed that Salt Typhoon, Ghost Emperor and FamousSparrow were the same group.
Alexandre Côté Cyr, Malware Researcher at ESET, commented: “It was the first public report that conflates the latter two groups. However, we see GhostEmperor and FamousSparrow as two distinct groups. There are few overlaps between the two but many discrepancies. Based on our data and analysis of the publicly available reports, FamousSparrow appears to be its own distinct cluster with loose links to the others.”
FamousSparrow Makes Comeback with New Toolset
ESET detected FamousSparrow when investigating suspicious activity on the network of a US trade group operating in the financial sector. The initial compromise occurred in June 2024.
To establish initial access to the compromised network, FamousSparrow utilized a web shell on an IIS server.
Although ESET could not identify the precise exploit used to deploy the web shells, both affected parties were operating on outdated versions of Windows Server and Microsoft Exchange, which have numerous publicly known exploits.
Additionally, the threat actor employed a combination of custom tools and malware, as well as those shared by China-aligned APT groups and publicly available sources.
The APT group utilized revamped tooling for the final payloads of these malicious campaigns, including two previously undocumented versions of the SparrowDoor backdoor.
“While these new versions exhibit significant upgrades, they can still be traced back directly to earlier, publicly documented versions. The loaders used in these attacks also present substantial code overlaps with samples previously attributed to FamousSparrow,” Côté Cyr said.
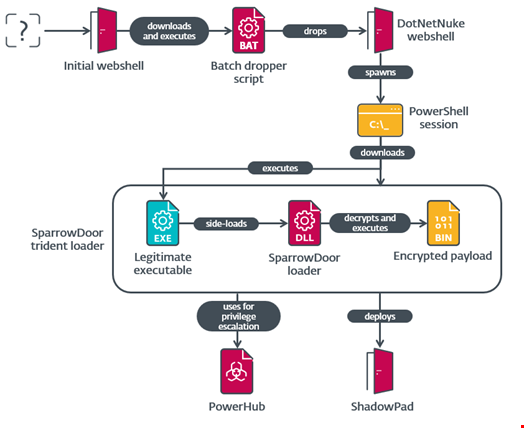
The campaigns observed by ESET also marked the first time FamousSparrow used the ShadowPad backdoor.
ShadowPad is a modular backdoor discovered in 2017 following a supply-chain attack on a popular piece of server management software attributed to APT41 (also known as Wicked Panda and Bronze Atlas), a Chinese dual espionage and cybercrime threat actor.
Since 2019, this malware has been shared among multiple Chinese threat actors, including Earth Akhlut and Earth Lusca.
Read now: China-Linked Weaver Ant Hackers Exposed After Four-Year Telco Infiltration
